Guide To Fill: Developer Registration and Assessment Form (DRAF)
Quick help guide to complete the Developer Registration Questionnaire.
Overview
Selling Partner API (SP-API) Overview: Video Link
Introduction to Amazon SP-API Roles: Video Link
Integrate with Amazon SP-API (Selling Partner API): Step 1 – Register as an SP-API developer: Video Link
Integrate with Amazon SP-API (Selling Partner API): Step 2 – Register an application for SP-API: Video Link
Guide to complete the Developer Registration and Assessment Form (DRAF):
Who should be filling the DRAF ?
DRAF should to be filled out by your IT/ Technical team after thoroughly going through Amazon’s policies that are listed below. DRAF will be assessed and in case your internal processes that are filled in the the form are not in alignment with Amazon's policies will be rejected. Make sure your internal processes are aligned with Amazon's Data Protection and Acceptable Use Policies before you submit the form. If you have further questions or need clarifications on any of these policies, feel free to reach out to Amazon’s Account Managers.
Data Protection Policy: (DPP) : LINK
Acceptable Use Policy: (AUP) : LINK
Where can I submit the DRAF ?
Once you are ready, submit your developer profile by following the below steps:
- Login to your Seller Central Account OR Developer Central Account (https://developercentral.amazon.com)
- In Seller Central Click the Partner Network on the menu bar and select “Develop Apps”.
- In Developer Central Account Click on Register and proceed to Proceed to Developer Profile.
- Click on “Proceed to Developer Profile”
- Next step after Proceed to Developer Profile is to fill contact Information.
Providing accurate contact details in the form is important for communication purposes
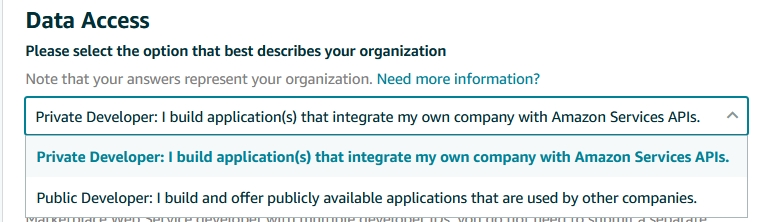
What Data Access do I require ?
Please select public/ private developer according to your requirements.
Private Developer: I build application(s) that integrate my own company with Amazon Services APIs.
Public Developer: I build and offer publicly available applications that are used by other companies.
Which Role do I require ?
Depending on your source of Order and Shipping requirement, you would either select one of these roles:
- Direct-to-Consumer Shipping (Restricted) - This role will allow to generate labels for the Order placed on Amazon marketplace and Orders placed on Seller's own website / other channels.
- Amazon Logistics - This role will only allow to generate labels for the Order placed on Seller own website / other channels.
Note - Amazon Logistics role is available only via Developer Central.
For additional details on roles please refer Amazon Shipping Roles help page.
Depending on the role selected, the DRAF questionnaire will provide list of additional questions which needs to be completed.
Which policies should I review while filling out the form ?
Please go through the following when filling the form:
1. List all outside parties with whom your organization shares Amazon Information and describe how your organization shares this information.
Please check and respond if Amazon information is shared with outside parties. Please address it as “Amazon data is not shared with any outside parties" if you do not share Amazon information outside your organization.
2. List all non-Amazon sources where you retrieve Amazon Information.
Please check and respond if you get Amazon information from non-amazon sources. Please respond it as “Not Applicable" if you do not retrieve Amazon information from any non-Amazon sources.
3. Describe the network protection controls used by your organization to restrict public access to databases, file servers, and desktop/developer endpoints.
Developers must implement network protection controls including network firewalls, network access control lists to deny access to unauthorized IP addresses. Developers must implement anti-virus and anti-malware software on end-user devices. Developers must restrict public access only to approved users. Refer DPP 1.1
4. Describe how your organization individually identifies employees who have access to Amazon Information, and restricts employee access to Amazon information on a need- to-know basis.
Developers must implement fine-grained access control mechanisms to allow granting rights to any party using the Application and the Application's operators following the principle of least privilege. Access to Information must be granted on a "need-to-know" basis. Developers must assign a unique ID to each person with computer access to Information. Developers must not create or use generic, shared, or default login credentials or user accounts. Developers must implement baselining mechanisms to ensure that at all times only the required user accounts access Information. Developers must review the list of people and services with access to Information every 90 days, and remove accounts that no longer require access. Refer DPP 1.3
5. Describe the mechanism your organization has in place to monitor and prevent Amazon Information from being accessed from employee personal devices (such as USB flash drives, cellphones) and how are you alerted in the event such incidents occur.
Developers must restrict employees and contractors from storing Information on personal devices. Developers will maintain and enforce "account lockout" by detecting anomalous usage patterns and log-in attempts, and disabling accounts with access to Information as needed. It is expected that you have a security alarm mechanism to monitor in case of Flash drive access is provided. If the employees are restricted from USB and Flash devices, please mention it here. Refer DPP 1.2
6. Provide your organization's privacy and data handling policies to describe how Amazon data is collected, processed, stored, used, shared and disposed. You may provide this in the form of a public website URL.
If your website has a privacy policy please provide the URL.
7. Describe where your organization stores Amazon Information at rest and provide details on any encryption algorithm used.
Developers must encrypt all PII at rest using at least AES-128 or RSA with 2048-bit key size or higher. The cryptographic materials (e.g., encryption/decryption keys) and cryptographic capabilities (e.g. daemons implementing virtual Trusted Platform Modules and providing encryption/decryption APIs) used for encryption of PII at rest must be only accessible to the Developer's processes and services. Refer DPP 2.4
8. Describe how your organization backups or archives Amazon Information and provide details on any encryption algorithm used.
Developers will retain PII for no longer than 30 days after order delivery and only for the purpose of, and as long as is necessary to (i) fulfill orders or to, (ii) calculate and remit taxes, and (iii) produce tax invoices. If a Developer is required by law to retain archival copies of PII for tax or similar regulatory purposes, PII must be stored as a "cold" or offline encrypted backup (e.g., not available for immediate or interactive use). Refer DPP 2.1
9. Describe how your organization monitors, detects and logs malicious activity in your application(s).
Developers must gather logs to detect security-related events to their applications and systems. including success or failure of the event, date and time, access attempts, data changes, and system errors Developers must implement this logging mechanism on all channels (e.g., service APIs, storage-layer APIs, administrative dashboards) providing access to Information. All logs must have access controls to prevent any unauthorized access and tampering throughout their lifecycle. Logs must not contain PII and must be retained for at least 90 days for reference in the case of a Security Incident. Developers must build mechanisms to monitor the logs and all system activities to trigger investigative alarms on suspicious actions (e.g., multiple unauthorized calls, unexpected request rate and data retrieval volume, and access to canary data records). Developers must implement monitoring alarms to detect if Information is extracted from its protected boundaries. Developers should perform investigation when monitoring alarms are triggered, and this should be documented in the Developer's Incident Response Plan. Refer DPP 2.6
10. Summarize the steps taken within your organization's incident response plan to handle database hacks, unauthorized access, and data leaks.
Developers must create and maintain a plan and/or runbook to detect and handle Security Incidents. Such plans must identify the incident response roles and responsibilities, define incident types that may affect Amazon, define incident response procedures for defined incident types, and define an escalation path and procedures to escalate Security Incidents to Amazon. Developers must review and verify the plan every six (6) months and after any major infrastructure or system change, including changes to the system, controls, operational environments, risk levels, and supply chain. Developers must notify Amazon (via email to [email protected]) within 24 hours of detecting Security Incident or suspecting that a Security Incident has occurred. Developers must investigate each Security Incident, and document the incident description, remediation actions, and associated corrective process/system controls implemented to prevent future recurrence. Developers must maintain the chain of custody for all evidences or records collected, and such documentation must be made available to Amazon upon request (if applicable). If a Security Incident occurred, Developers cannot represent or speak on behalf of Amazon to any regulatory authority or customers unless Amazon specifically requests in writing that the Developer do so. Refer DPP 1.6
11. How do you enforce password management practices throughout the organization as it relates to required length, complexity (upper/lower case, numbers, and special character), and expiration period?
Developers must establish minimum password requirements for personnel and systems with access to Information. Password requirements must be a minimum of twelve (12) characters, not include any part of the user’s name, mix of upper-case letters, lower-case letters, numbers, and special characters, including minimum requirements for each. Developers must establish a minimum password age of 1-day and a maximum 365-day password expiration for all users. Developers must ensure that Multi-Factor Authentication (MFA) is required for all user accounts Developer must ensure that API keys provided by Amazon are encrypted and only required employees have access to them. Refer DPP 1.4
12. How is Personally Identifiable Information (PII) protected during testing?
Developers must maintain separate test and production environments and protect PII data during testing. If you do not use real PII data, please mention it as "We will use Amazon Shipping Sandbox environment which contains dummy data for testing. We don’t use real person data out of the live platforms during testing”. Refer DPP 2.5
13. What measures are taken to prevent exposure of credentials?
Developers must not hardcode sensitive credentials in their code, including encryption keys, secret access keys, or passwords. Sensitive credentials must not be exposed in public code repositories. Developers must maintain separate test and production environments. Refer DPP 2.5
14. How do you track the remediation progress of findings identified from vulnerability scans and penetration tests?
Developers must create and maintain a plan and/or runbook to detect and remediate vulnerabilities. Developers must protect physical hardware containing PII from technical vulnerabilities by performing vulnerability scans and remediating appropriately. Refer DPP 2.7
15. How do you address code vulnerabilities identified in the development lifecycle and during runtime?
Developers must conduct vulnerability scanning or penetration tests at least every 180 days and scan code for vulnerabilities prior to each release. Furthermore, Developers must control changes to the storage hardware by testing, verifying changes, approving changes, and restricting access to who may perform those actions. Refer DPP 2.7
16. Who is responsible for change management and how is their access granted? Please specify the job title.
Describe the role of who is responsible for change management requests and what is the change management tool used for tracking the changes and how access is granted to these roles.
Updated 2 months ago
